$16 Million Fine For T-Mobile: Details Of Three Years Of Data Security Lapses

Table of Contents
The Extent of T-Mobile's Data Security Failures
Years of Neglect: A Timeline of Unchecked Vulnerabilities
The T-Mobile data breach wasn't a single event; it was the culmination of years of unaddressed security issues. The lapses extended over a three-year period, allowing attackers repeated opportunities to exploit vulnerabilities.
- 2020: Initial reports surfaced indicating potential weaknesses in T-Mobile's systems.
- 2021: Multiple security incidents occurred, exposing sensitive customer data. Specific vulnerabilities, though not publicly detailed, likely included weaknesses in network security and outdated software.
- 2022: The extent of the data security lapse became fully apparent, leading to the substantial $16 million fine. The compromised data included personal information such as names, addresses, social security numbers, and financial details.
These failures underscore a pattern of neglect and a lack of proactive measures to secure sensitive customer data. The sheer duration of these lapses allowed attackers ample time to penetrate and exploit system vulnerabilities.
The Role of Third-Party Vendors: Shared Responsibility and Accountability
The involvement of third-party vendors in the T-Mobile data breach remains a point of investigation. While the specifics may not be fully public, the incident highlights the critical risks associated with relying on external vendors for data security.
- Potential vulnerabilities in the security protocols of the third-party vendors could have been exploited.
- Breaches of contract agreements related to data security may have contributed to the lapses.
- The reliance on third-party vendors underscores the need for meticulous vetting, ongoing monitoring, and robust contract clauses emphasizing data security responsibilities.
This case serves as a cautionary tale for businesses that outsource parts of their data security. Careful selection and consistent oversight of third-party vendors are paramount to mitigate the risk of data security lapses.
Lack of Proactive Security Measures: A Recipe for Disaster
The T-Mobile case illustrates the catastrophic consequences of insufficient proactive security measures. The absence of preventative strategies and inadequate security protocols played a significant role in the breach.
- Insufficient encryption of sensitive data left it vulnerable to attack.
- Outdated software and systems lacked necessary security patches, creating exploitable weaknesses.
- A lack of comprehensive employee training on data security best practices allowed for human error to contribute to the problem.
These failures starkly contrast with industry best practices, highlighting the crucial need for robust security architectures, regular security assessments, and continuous monitoring of vulnerabilities.
The Impact of the Data Security Lapses
Financial Penalties: A Costly Lesson Learned
The $16 million fine imposed on T-Mobile is a significant financial penalty, but it's only a fraction of the total cost.
- Investigations into the breach incurred substantial expenses.
- Remediation efforts to secure systems and mitigate further damage added to the financial burden.
- Potential legal fees and settlements with affected customers will undoubtedly increase the overall cost.
- The impact on T-Mobile's stock price reflects investor concern over the company's data security practices.
This financial toll underscores the significant price of neglecting data security.
Reputational Damage: Erosion of Trust and Customer Loyalty
Beyond the financial repercussions, T-Mobile suffered severe reputational damage. The data breach eroded customer trust and negatively impacted the company's brand image.
- Loss of customers due to concerns about data security.
- Negative publicity significantly impacted public perception.
- Future business opportunities may be compromised due to the loss of confidence.
- Consumer lawsuits further exacerbated the reputational fallout.
The long-term effects of this reputational damage will take significant time and resources to repair.
Customer Impact: The Human Cost of Data Breaches
The most significant impact of T-Mobile's data security lapse was on its customers. The exposure of personal and financial information created substantial risks for those affected.
- Increased risk of identity theft and financial fraud.
- Potential for significant financial losses due to fraudulent activities.
- Emotional distress and anxiety associated with the breach.
- T-Mobile offered credit monitoring services to affected customers, but this is a mere band-aid to the deeper wounds caused by the lapse.
The human cost of data breaches cannot be overlooked; the consequences for victims extend far beyond financial losses.
Lessons Learned and Best Practices for Data Security
Importance of Proactive Security: A Culture of Prevention
The T-Mobile data breach underscores the critical need for a proactive approach to data security. This includes:
- Regular security assessments to identify and address vulnerabilities.
- Penetration testing to simulate real-world attacks and expose weaknesses.
- Robust vulnerability management processes to ensure timely patching and remediation.
A proactive security posture prevents breaches before they occur, significantly reducing the risk and associated costs.
Employee Training and Awareness: Human Element of Security
Human error plays a significant role in many data breaches. Comprehensive employee training is crucial:
- Educate employees on recognizing and responding to phishing attacks.
- Implement strong password policies and multi-factor authentication.
- Promote a strong security culture where employees are actively involved in protecting company data.
Investing in employee training is an effective way to mitigate human-error-related security risks.
Third-Party Vendor Risk Management: Due Diligence and Oversight
Managing the risks associated with third-party vendors is crucial:
- Rigorous vetting process before engaging any vendor.
- Regular monitoring of vendor security practices and compliance.
- Clearly defined contracts that specify security responsibilities and liabilities.
Robust oversight of third-party vendors is vital for maintaining a secure data environment.
Compliance and Regulations: Staying Ahead of the Curve
Staying compliant with relevant data privacy regulations is non-negotiable:
- Understanding and adhering to regulations like GDPR, CCPA, and others.
- Implementing appropriate data protection measures to meet regulatory requirements.
- Staying updated on evolving regulations and best practices.
Compliance not only prevents penalties but also demonstrates a commitment to data security.
Conclusion: Preventing Future T-Mobile-like Data Security Lapses
T-Mobile's $16 million fine serves as a stark reminder of the severe consequences of neglecting data security. The company's prolonged data security lapses resulted in significant financial penalties, reputational damage, and substantial harm to its customers. To avoid costly data security lapses, businesses must prioritize proactive security measures, invest in employee training, and implement robust third-party vendor risk management programs. Investing in comprehensive cybersecurity solutions and fostering a strong security culture are crucial to preventing similar incidents and safeguarding sensitive data. Don't let your business become the next headline; learn from T-Mobile's mistakes and implement robust data security solutions to prevent future lapses.

Featured Posts
-
 Fox Sports Inaugural Indy Car Season What To Expect
May 04, 2025
Fox Sports Inaugural Indy Car Season What To Expect
May 04, 2025 -
 I Emma Stooyn I Anatreptiki Emfanisi Poy Sarose Deite To Forema
May 04, 2025
I Emma Stooyn I Anatreptiki Emfanisi Poy Sarose Deite To Forema
May 04, 2025 -
 Euphoria Star Sydney Sweeney Wears Wedding Dress Post Engagement Breakup
May 04, 2025
Euphoria Star Sydney Sweeney Wears Wedding Dress Post Engagement Breakup
May 04, 2025 -
 Legal Battle E Bay Banned Chemicals And The Limits Of Section 230
May 04, 2025
Legal Battle E Bay Banned Chemicals And The Limits Of Section 230
May 04, 2025 -
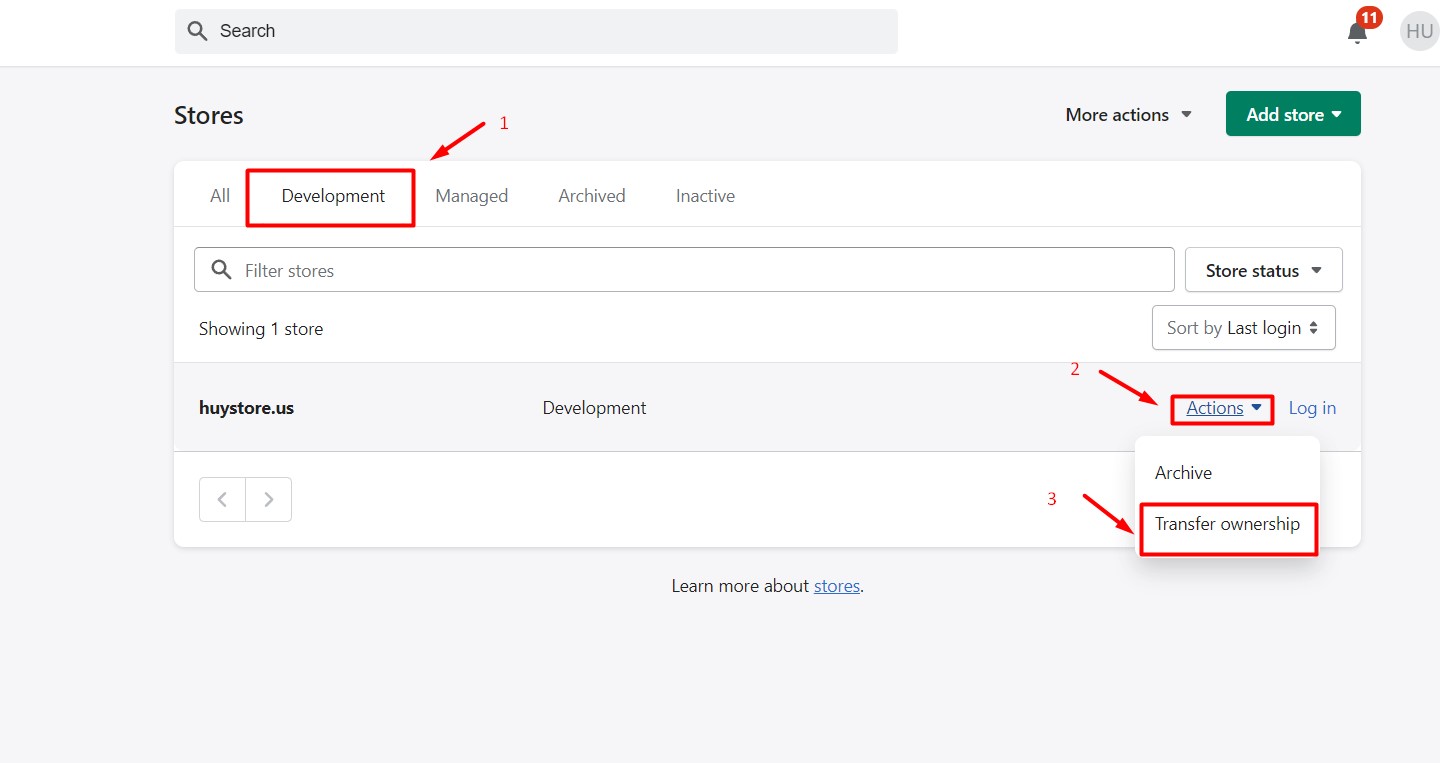 Understanding The Shift To A Lifetime Revenue Share For Shopify Developers
May 04, 2025
Understanding The Shift To A Lifetime Revenue Share For Shopify Developers
May 04, 2025
