Cybercriminal Made Millions Targeting Executive Office 365 Accounts

Table of Contents
The Modus Operandi: How the Cybercriminal Targeted Executive Office 365 Accounts
The cybercriminal employed a multi-pronged approach, combining sophisticated social engineering techniques with exploitation of common security weaknesses.
Phishing and Spear Phishing Attacks
The attacks primarily relied on highly targeted phishing and spear-phishing campaigns. These weren't generic phishing emails; they were meticulously crafted to appear legitimate and tailored to individual executives.
- Examples of lures used: Emails mimicked urgent requests from known clients, invoices from trusted suppliers, or notifications from internal systems.
- Email spoofing techniques: The cybercriminal cleverly spoofed email addresses, making them almost indistinguishable from genuine communications. They used techniques like domain name hijacking and typosquatting to trick recipients.
- Social engineering: The emails preyed on urgency, fear, and trust, leveraging psychological manipulation to pressure recipients into clicking malicious links or revealing credentials.
Keywords: "Office 365 phishing," "executive spear phishing," "credential harvesting"
Exploiting Weak Passwords and Security Gaps
The success of the attacks hinged on exploiting weak security practices within the target organizations. This included a reliance on weak passwords and a lack of robust security measures.
- Examples of weak passwords: Many executives used easily guessable passwords or reused passwords across multiple accounts.
- Reasons for MFA bypass: The lack of multi-factor authentication (MFA) meant that even if credentials were compromised, there was no second layer of security to prevent unauthorized access.
- Vulnerabilities exploited in Office 365 apps: Outdated software and unpatched vulnerabilities in various Office 365 applications also contributed to the successful breaches.
Keywords: "Office 365 security vulnerabilities," "multi-factor authentication," "password management."
Data Exfiltration Techniques
Once access was gained, the cybercriminal employed various methods to exfiltrate sensitive data, ensuring the operation remained undetected for an extended period.
- Examples of data exfiltration methods: The attacker utilized cloud storage services and file-sharing platforms to transfer stolen data, masking it within legitimate files or using encrypted channels.
- Data transfer and security: The exfiltrated data was likely transferred through encrypted channels to avoid detection and was stored on encrypted servers to maintain control.
Keywords: "data breach," "data exfiltration," "Office 365 data security."
The Financial Impact: Millions Made from Compromised Executive Office 365 Accounts
The consequences of the attack extended far beyond the initial compromise. The cybercriminal leveraged the stolen data for substantial financial gain.
Ransomware and Extortion
The stolen data, including sensitive financial information and confidential business plans, was used to extort millions from the targeted businesses.
- Examples of demands: Ransom demands varied, ranging from hundreds of thousands to millions of dollars, depending on the sensitivity of the stolen data and the potential reputational damage.
- Methods of payment: Cryptocurrencies were likely used for payment to maintain anonymity and hinder tracing.
- Impact on business operations: The attacks caused significant disruption to business operations, resulting in lost productivity, delayed projects, and potential legal repercussions.
Keywords: "ransomware attack," "cyber extortion," "Office 365 ransomware."
Financial Losses Beyond Ransom Payments
The financial losses extended far beyond the ransom payments themselves.
- Quantifying the financial damage: The indirect costs, encompassing legal fees for investigations and regulatory compliance, reputational damage, loss of customer trust, and the cost of recovery efforts, often exceeded the ransom demands several times over.
Keywords: "data breach costs," "reputational damage," "business interruption."
Lessons Learned and Best Practices for Protecting Executive Office 365 Accounts
Protecting your organization from similar attacks requires a proactive and multi-layered approach.
Strengthening Password Security and Implementing MFA
Strong password policies and multi-factor authentication are non-negotiable.
- Implementing these measures: Enforce complex passwords with a minimum length and character variety, and mandate the use of a strong password manager. Deploy MFA across all Office 365 accounts, requiring authentication from multiple devices or methods.
Keywords: "strong passwords," "multi-factor authentication," "password management best practices."
Enhancing Security Awareness Training
Regular and comprehensive security awareness training is paramount, especially for executives who are frequent targets.
- Practical training methods and topics: Conduct phishing simulations, deliver regular training on identifying suspicious emails, and educate employees on social engineering tactics.
Keywords: "security awareness training," "phishing awareness," "cybersecurity training."
Regular Security Audits and Vulnerability Assessments
Regular security audits and vulnerability assessments are crucial for proactive identification and mitigation of weaknesses.
- Frequency of audits and types of assessments: Conduct regular security audits of your Office 365 environment at least annually, and supplement these with penetration testing to simulate real-world attacks.
Keywords: "Office 365 security audit," "vulnerability assessment," "penetration testing."
Conclusion
This case study demonstrates the devastating impact of sophisticated cyberattacks targeting Executive Office 365 Accounts. The financial losses incurred and the sophisticated techniques employed highlight the urgent need for robust security measures. Don't wait for a similar attack to cripple your business. Take immediate steps to secure your Office 365 environment by implementing MFA, investing in comprehensive security awareness training, and conducting regular security audits. Protect your executive accounts and your bottom line by prioritizing Office 365 account security today. Proactive measures to protect your executive accounts are the best defense against this growing threat.

Featured Posts
-
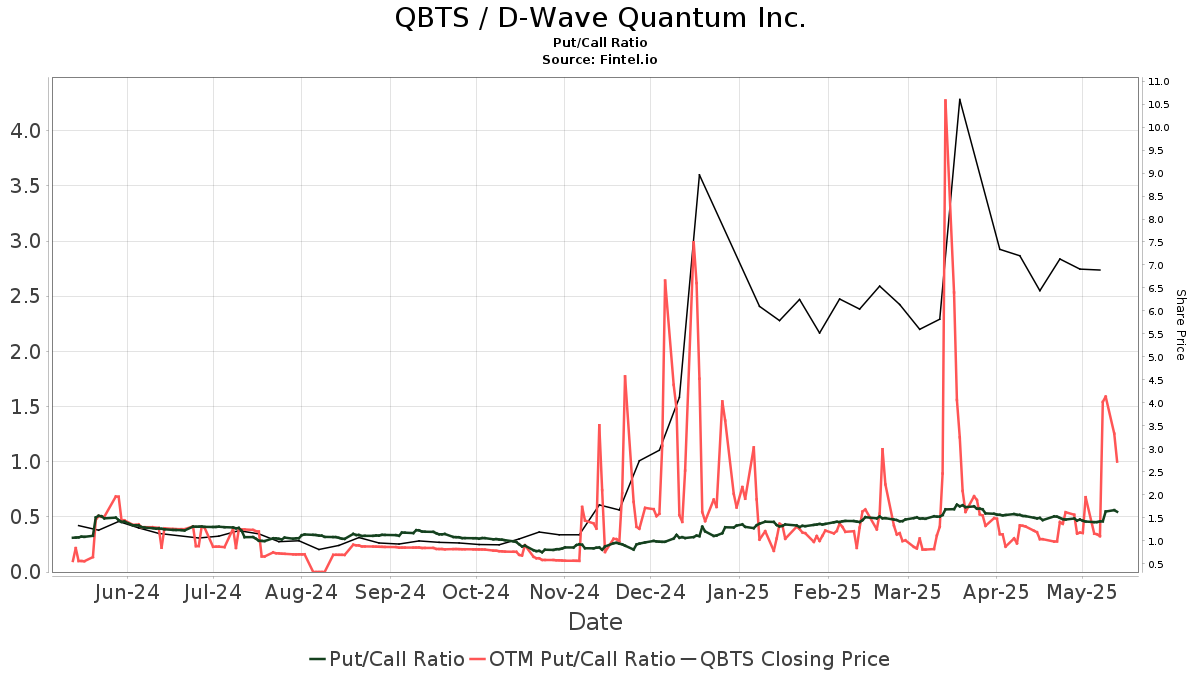 Analyzing The D Wave Quantum Qbts Stock Decrease On Thursday
May 20, 2025
Analyzing The D Wave Quantum Qbts Stock Decrease On Thursday
May 20, 2025 -
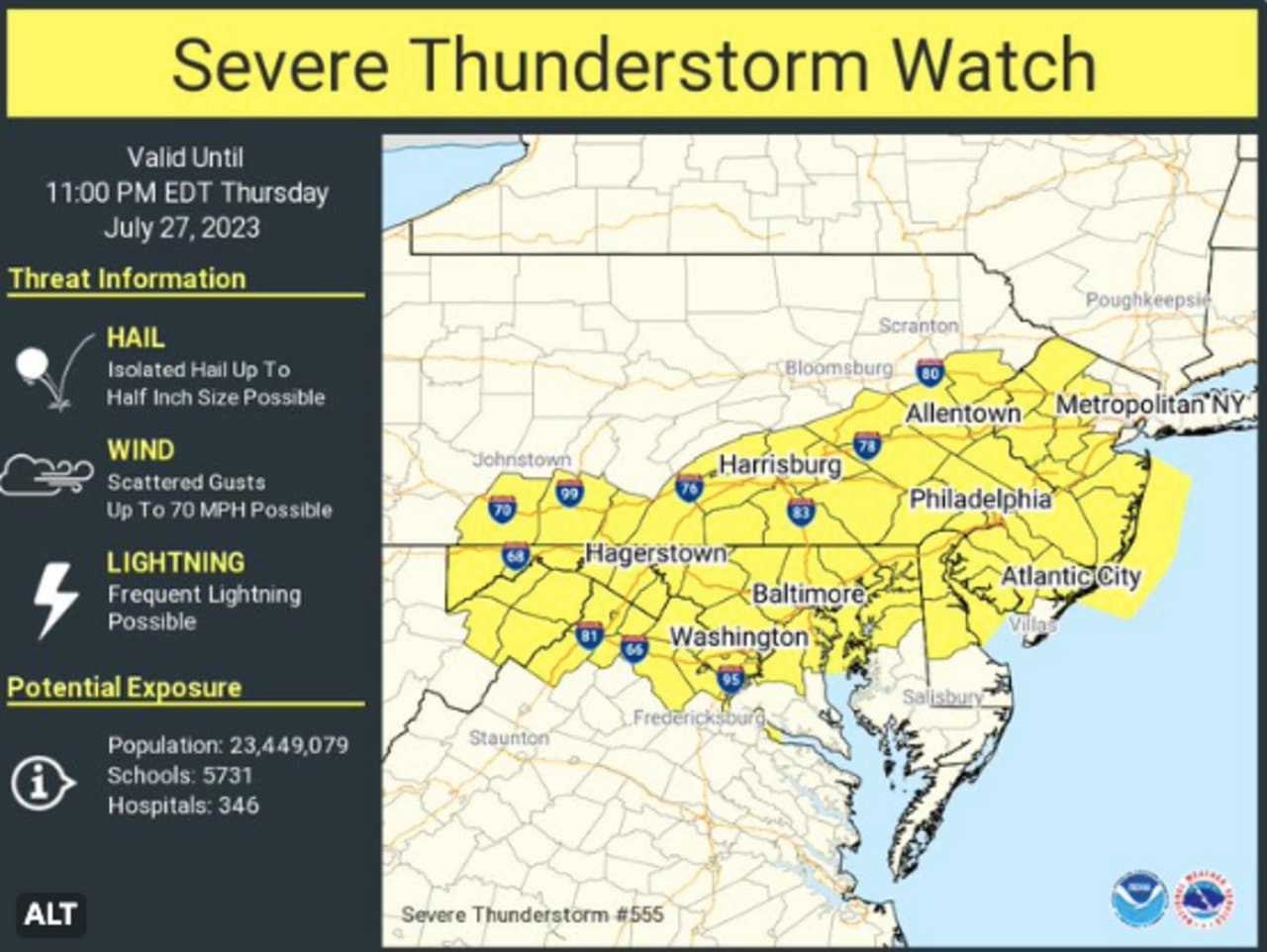 Severe Weather Watch Recognizing And Responding To High Wind Events
May 20, 2025
Severe Weather Watch Recognizing And Responding To High Wind Events
May 20, 2025 -
 Dusan Tadic Fenerbahce Ye Yeni Bir Cag
May 20, 2025
Dusan Tadic Fenerbahce Ye Yeni Bir Cag
May 20, 2025 -
 Schumacher Bunic O Noua Generatie In Familia Legendarului Pilot
May 20, 2025
Schumacher Bunic O Noua Generatie In Familia Legendarului Pilot
May 20, 2025 -
 Chinas Plan For A Space Based Supercomputer Challenges And Opportunities
May 20, 2025
Chinas Plan For A Space Based Supercomputer Challenges And Opportunities
May 20, 2025
