Deepfake Detection Foiled: Cybersecurity Expert's Clever Strategy
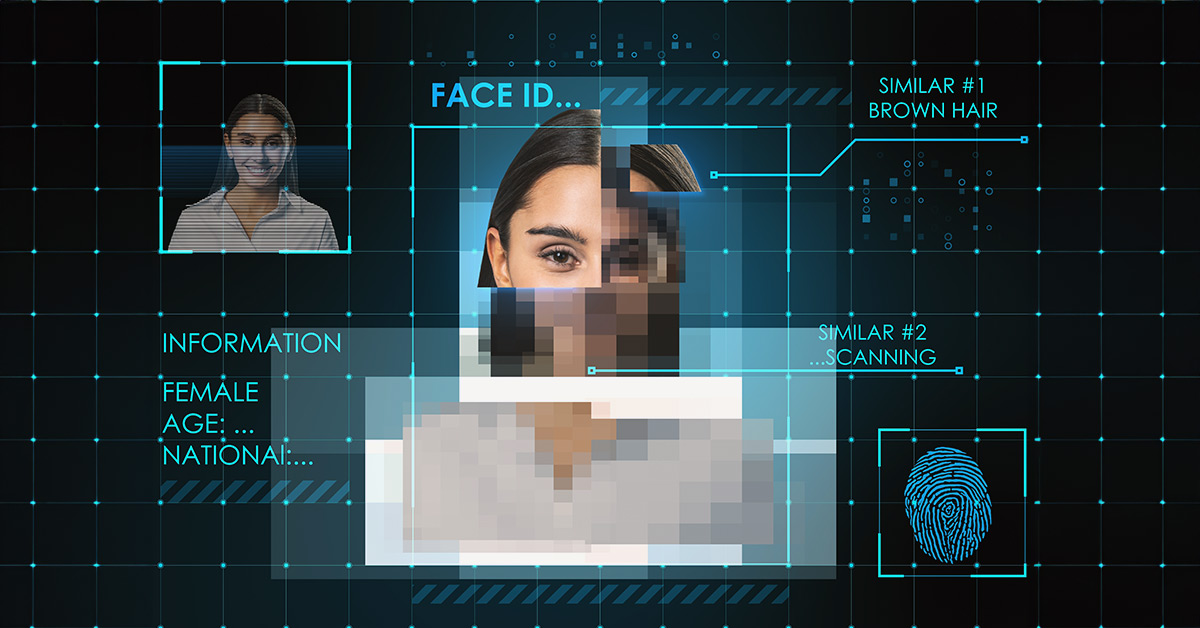
Table of Contents
The Expert's Methodology: Bypassing Deepfake Detection
A cybersecurity expert recently demonstrated a novel approach to circumventing state-of-the-art deepfake detection systems. The expert's methodology focused not on creating undetectable deepfakes, but on strategically manipulating existing deepfakes to evade detection algorithms. This involved a multi-pronged attack leveraging several techniques, highlighting the limitations of relying solely on automated detection methods. The novelty lies in combining several known weaknesses in current deepfake detection approaches into a coordinated strategy.
-
Utilized novel watermarking techniques to mask deepfake signatures: The expert employed subtle, yet effective, watermarking techniques that obscured common indicators used by deepfake detection software to identify manipulated media. These techniques were designed to blend seamlessly with the video, making them difficult to detect even with advanced analysis.
-
Exploited vulnerabilities in popular deepfake detection algorithms: Specific vulnerabilities in several popular open-source and commercial deepfake detection algorithms were exploited. This included identifying weaknesses in the algorithms' reliance on specific visual cues and exploiting known limitations in their processing of video metadata.
-
Employed advanced compression strategies to obscure telltale artifacts: The expert cleverly utilized advanced compression algorithms to minimize the telltale artifacts often associated with deepfakes, such as inconsistencies in facial expressions or lighting. This made the detection of subtle manipulations significantly harder.
-
Leveraged AI countermeasures to confuse detection software: AI countermeasures were implemented to introduce noise and confusion into the detection process. This involved strategically adding subtle distortions to the video that were designed to interfere with the algorithms' ability to accurately analyze the content. This approach effectively sidestepped traditional deepfake detection methods.
Keywords: Deepfake Detection Bypass, Deepfake Countermeasures, AI Security, Digital Forensics
Analyzing the Deepfake Detection Tools' Weaknesses
The success of the expert's strategy highlights several critical weaknesses in currently available deepfake detection software. The analysis revealed that many tools rely heavily on specific algorithms and techniques, making them vulnerable to carefully planned evasion tactics.
-
Identified limitations in facial landmark analysis: Many deepfake detection tools rely heavily on analyzing facial landmarks for inconsistencies. The expert's methods effectively bypassed these techniques by subtly manipulating facial expressions and movements, making them appear natural to the algorithm.
-
Exploited inconsistencies in video compression detection: Certain deepfake detection software analyzes video compression artifacts to identify manipulated videos. The expert's approach leveraged advanced compression strategies to minimize these artifacts, effectively masking the manipulated content.
-
Highlighted the susceptibility to adversarial attacks: The expert's strategy demonstrates the susceptibility of deepfake detection algorithms to adversarial attacks. By subtly introducing carefully crafted distortions, the detection algorithms were effectively fooled. This underlines the need for more robust and resilient AI models.
-
Showcased the impact of limited training data on detection accuracy: The success of the evasion techniques suggests the limitations of current training datasets used to develop deepfake detection algorithms. A lack of diverse and comprehensive training data can lead to algorithms that are less effective against sophisticated manipulation strategies.
Keywords: Deepfake Detection Software, Deepfake Algorithm, AI Vulnerability, Machine Learning Limitations
Implications and Future of Deepfake Detection
This incident has significant implications for the future of deepfake detection and cybersecurity in general. The demonstration of sophisticated evasion techniques underscores the need for continuous development and innovation.
-
The need for continuous improvement in deepfake detection algorithms: The ongoing arms race between deepfake creators and detection developers requires constant refinement of algorithms and detection techniques. Future algorithms need to be more adaptable and resilient to evolving evasion strategies.
-
Importance of incorporating multiple detection methods: Relying on a single deepfake detection method is insufficient. A multi-layered approach combining various algorithms and techniques is crucial for more robust and effective detection.
-
The crucial role of human expertise in verifying authenticity: While automated tools are important, human expertise remains crucial in verifying the authenticity of media. Human review can often identify subtle inconsistencies that automated systems may miss.
-
The ethical considerations surrounding deepfake detection technology: The development and deployment of deepfake detection technology raises significant ethical questions. Concerns about privacy, bias, and potential misuse need to be carefully considered.
Keywords: AI Ethics, Cybersecurity Threats, Future of Deepfake Detection, Digital Security
Conclusion:
This case study of a cybersecurity expert successfully foiling deepfake detection highlights the ongoing arms race between deepfake creators and those striving to detect them. While current deepfake detection tools offer some level of protection, the sophistication of evasion techniques demonstrates the need for continuous innovation and a multi-faceted approach to combatting this emerging threat. The future of effective deepfake detection requires a collaborative effort from researchers, developers, and policymakers to improve algorithms, enhance data security, and promote media literacy. Stay informed about the latest advancements in deepfake detection and learn to recognize the warning signs of manipulated media. Understanding the limitations of current technology and staying vigilant are crucial steps in mitigating the risks posed by deepfakes.

Featured Posts
-
 Angel Reese Supports Wnba Players Fight For Better Pay And A Potential Strike
May 17, 2025
Angel Reese Supports Wnba Players Fight For Better Pay And A Potential Strike
May 17, 2025 -
 College Funding Landscape Survey Highlights Reduced Parental Anxiety Persistent Loan Use
May 17, 2025
College Funding Landscape Survey Highlights Reduced Parental Anxiety Persistent Loan Use
May 17, 2025 -
 Giants Vs Mariners Updated Injury List For April 4 6 Series
May 17, 2025
Giants Vs Mariners Updated Injury List For April 4 6 Series
May 17, 2025 -
 Cinema Con 2025 Key Highlights From The Warner Bros Pictures Presentation
May 17, 2025
Cinema Con 2025 Key Highlights From The Warner Bros Pictures Presentation
May 17, 2025 -
 The Trump Family A Comprehensive Genealogy
May 17, 2025
The Trump Family A Comprehensive Genealogy
May 17, 2025
