Delete Your Digital Footprint: Strategies For Online Privacy

Table of Contents
Managing Your Social Media Presence
Social media platforms are significant contributors to our digital footprint. Effectively managing your presence on these platforms is crucial for minimizing your online exposure.
Deactivating or Deleting Accounts
Deactivating versus deleting your accounts presents a crucial choice. Deactivating temporarily hides your profile, allowing you to reactivate later. Deleting permanently removes your account and data.
- Steps to Deactivate/Delete: Each platform has its own process. Check the help section of Facebook, Instagram, Twitter, and other platforms for detailed instructions.
- Account Recovery Implications: Remember, deleting an account often means irreversible loss of data. Be absolutely certain before proceeding. Deactivation allows for easier recovery.
- Impact on Networking: Deleting accounts could affect your professional and personal connections. Consider the implications carefully.
Reviewing and Removing Old Posts and Content
Past posts and content can contain embarrassing or outdated information that could negatively impact your reputation. Regular review and removal are essential.
- Identifying Problematic Content: Look for old photos, controversial opinions, or anything that could be misconstrued or used against you.
- Tools for Bulk Deletion: Some platforms offer tools to help you delete multiple posts simultaneously. Explore these options to streamline the process.
- Privacy Settings: Use privacy settings to control who sees your content. Limit visibility to close friends and family.
Limiting Information Shared Publicly
Sharing personal information publicly increases your vulnerability. Be mindful of what you share online.
- Sensitive Information to Avoid: Avoid sharing your full address, phone number, financial details, or other sensitive information.
- Strong Privacy Settings: Utilize the robust privacy settings offered by social media platforms to limit who can access your information.
Controlling Your Search Engine Results
Search engines play a crucial role in shaping your online presence. Understanding how to manage your search engine results is vital.
Understanding Google's Search Results
Google's algorithm considers numerous factors when displaying search results. Your online activity, website links, and even social media posts all contribute.
- "Right to be Forgotten": While you may request removal of information under certain circumstances (e.g., outdated or inaccurate information), Google's "right to be forgotten" policy has limitations.
Removing Information from Search Engines
You can request the removal of outdated or inaccurate information from search engine results.
- Google's Removal Tools: Google provides tools to request removal of content from its search results. The process involves submitting a request, which Google may or may not grant.
- Contacting Websites: If the information appears on a website, contact the website owner to request its removal.
Using Privacy-Focused Search Engines
Consider alternative search engines that prioritize user privacy, such as DuckDuckGo or Startpage. These engines do not track your searches.
Securing Your Online Accounts and Data
Robust security practices are crucial for protecting your online identity and data.
Strong Passwords and Two-Factor Authentication
Strong and unique passwords are your first line of defense. Two-factor authentication adds an extra layer of security.
- Password Managers: Use password managers to generate and store strong, unique passwords for each account.
- Password Security Best Practices: Use a mix of uppercase and lowercase letters, numbers, and symbols. Avoid using easily guessable passwords.
- Two-Factor Authentication (2FA): Enable 2FA wherever possible. This requires a second verification step, such as a code sent to your phone or email.
Regularly Updating Software and Security Patches
Outdated software is vulnerable to security breaches. Regular updates are essential.
- Automatic Updates: Enable automatic updates whenever possible to ensure your software is always up-to-date.
- Regularly Checking for Updates: Periodically check for updates manually, especially for less frequently updated software.
Using VPNs and other Privacy Tools
VPNs (Virtual Private Networks) and other privacy tools can enhance your online security and anonymity.
- Types of VPNs: Various VPNs offer different levels of security and features. Research and choose a reputable provider.
- Considerations When Choosing a VPN: Consider factors such as speed, security features, and privacy policy when selecting a VPN.
Protecting Your Digital Footprint on Other Platforms
Beyond social media and search engines, your digital footprint extends across various online platforms.
Online Forums and Communities
Be mindful of what you share on online forums and communities.
- Using Pseudonyms: Consider using pseudonyms or usernames to maintain a degree of anonymity.
- Mindful Public Sharing: Think before posting; what you share publicly may remain online indefinitely.
Online Shopping and Transactions
Protecting your data during online purchases is paramount.
- Secure Payment Methods: Use secure payment methods like PayPal or credit cards with robust fraud protection.
- Reviewing Privacy Policies: Carefully review the privacy policies of online retailers before making purchases.
Email and Communication
Secure your emails and other forms of online communication.
- Strong Passwords: Use strong, unique passwords for your email accounts.
- Two-Factor Authentication: Enable two-factor authentication for added security.
Conclusion: Taking Control of Your Digital Footprint
Deleting or minimizing your digital footprint is an ongoing process requiring proactive measures. By managing your social media presence, controlling search engine results, securing your online accounts, and protecting your information across various platforms, you can significantly reduce your online vulnerability and reclaim your privacy. The long-term benefits of managing your online privacy are substantial, protecting your reputation, security, and peace of mind. Start implementing these strategies today to effectively delete your digital footprint and take control of your online privacy. Share this article with others who are concerned about their digital footprint and help spread awareness of online privacy best practices!

Featured Posts
-
 Broadcoms Proposed V Mware Price Hike A 1 050 Jump Concerns At And T
Apr 23, 2025
Broadcoms Proposed V Mware Price Hike A 1 050 Jump Concerns At And T
Apr 23, 2025 -
 Selling Sunset Star Exposes La Landlord Price Gouging After Fires
Apr 23, 2025
Selling Sunset Star Exposes La Landlord Price Gouging After Fires
Apr 23, 2025 -
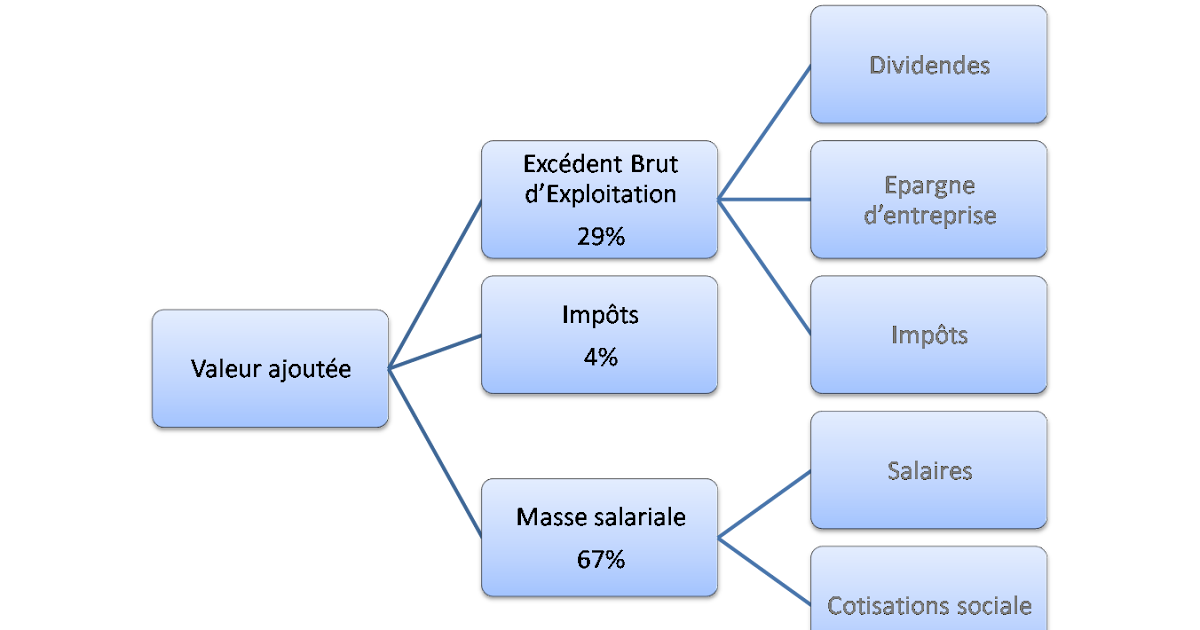 Valeur Ajoutee D Infotel Experiences Clients Et Resultats Concrets
Apr 23, 2025
Valeur Ajoutee D Infotel Experiences Clients Et Resultats Concrets
Apr 23, 2025 -
 Ankara Iftar Ve Sahur Saatleri 10 Mart 2025 Pazartesi
Apr 23, 2025
Ankara Iftar Ve Sahur Saatleri 10 Mart 2025 Pazartesi
Apr 23, 2025 -
 Trumps Attack On Jerome Powell Calls For Fed Chairs Termination
Apr 23, 2025
Trumps Attack On Jerome Powell Calls For Fed Chairs Termination
Apr 23, 2025
