Execs' Office 365 Accounts Breached: Millions Made, Feds Say
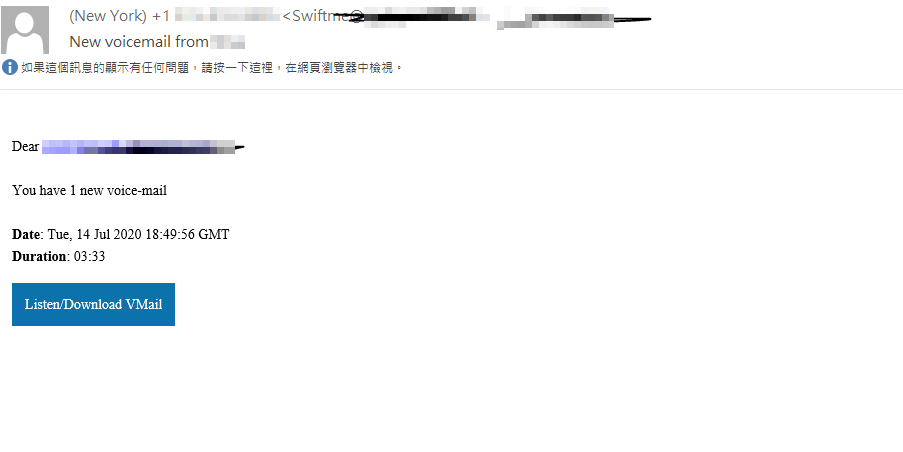
Table of Contents
The Scale and Impact of the Office 365 Breaches
The financial consequences of compromised executive Office 365 accounts are staggering. These data breaches represent a significant cybersecurity threat, impacting not only the bottom line but also the long-term reputation and stability of affected organizations. The impact extends far beyond simple financial losses.
- Millions of dollars lost: Fraudulent transactions, wire transfers, and other financial schemes initiated from compromised accounts have resulted in millions of dollars in losses for affected companies. The cost of an executive account compromise can be exceptionally high due to the access these accounts often provide.
- Significant reputational damage: News of a data breach, particularly one involving executive accounts, severely damages a company's reputation. This leads to a loss of investor confidence, potential stock devaluation, and erosion of customer trust, impacting future business prospects.
- Exposure of sensitive company data: Executive accounts often hold access to highly sensitive information, including intellectual property, strategic plans, confidential client data, and merger & acquisition discussions. This exposure can cause irreparable harm.
- Disruption of business operations: Compromised email systems and account lockouts can significantly disrupt daily operations, leading to lost productivity, delays in projects, and overall operational inefficiencies. The cost of recovery and remediation can be substantial.
Methods Used by Cybercriminals
Cybercriminals employ increasingly sophisticated methods to breach Office 365 accounts, particularly those belonging to executives. These methods often exploit human vulnerabilities and leverage advanced techniques to gain unauthorized access.
- Phishing attacks: Highly targeted phishing emails, often personalized to appear legitimate, are used to trick executives into revealing their credentials. These attacks utilize convincing lures and exploit social engineering principles.
- Spear phishing attacks: These attacks go beyond generic phishing, employing highly specific information about the target to make the email appear even more authentic. This requires significant reconnaissance and demonstrates a high level of sophistication.
- Credential stuffing attacks: Cybercriminals leverage credentials obtained from previous data breaches to attempt to access accounts. This underscores the importance of using unique, strong passwords and multi-factor authentication.
- Malware: Malware, such as keyloggers and remote access Trojans (RATs), can be used to gain persistent access to compromised accounts and steal sensitive information. This allows for long-term exploitation and data exfiltration.
- Social engineering tactics: Cybercriminals often employ social engineering tactics to manipulate users into revealing their credentials or downloading malware. This emphasizes the need for robust security awareness training for all employees.
The Federal Investigation and its Implications
The ongoing federal investigations into the widespread Office 365 breaches highlight the seriousness of the issue and the potential for significant legal ramifications. These investigations will likely lead to increased regulatory scrutiny and stricter enforcement actions.
- Details of the investigations: Federal agencies are actively investigating these breaches, examining the methods used, the extent of the damage, and the responsibility of affected organizations.
- Legal ramifications: Companies that fail to adequately protect their systems and data face potential lawsuits, significant fines, and reputational damage. Non-compliance with data protection regulations can lead to severe penalties.
- Increased regulatory scrutiny: The breaches will undoubtedly increase regulatory scrutiny on cybersecurity practices and compliance with regulations such as GDPR and CCPA.
- Potential for significant fines and penalties: Companies found to be negligent in their security practices may face substantial fines and penalties, adding to the already significant financial burden of a breach.
Lessons Learned and Best Practices
The Office 365 breaches serve as a stark reminder of the importance of robust cybersecurity practices. Implementing the following best practices can significantly reduce the risk of future attacks.
- Implement robust multi-factor authentication (MFA): MFA adds an extra layer of security, significantly reducing the likelihood of unauthorized access even if credentials are compromised. This is critical for executive accounts.
- Provide comprehensive cybersecurity awareness training: Educating employees about phishing attacks, social engineering tactics, and other cybersecurity threats is crucial in preventing breaches. Regular training is key to keeping employees informed.
- Regularly update software and security patches: Keeping software and systems up-to-date with the latest security patches is essential to mitigating vulnerabilities. This should be a continuous process, not a one-time event.
- Enforce strong password policies and implement password managers: Strong, unique passwords are essential, and password managers can help employees manage complex passwords securely. Password reuse should be strictly prohibited.
- Conduct regular security audits and vulnerability assessments: Regular security audits and vulnerability assessments help identify weaknesses in systems and processes, allowing for proactive remediation. This proactive approach is vital.
- Develop and test incident response plans for data breaches: Having a well-defined incident response plan in place allows organizations to respond effectively and efficiently in the event of a data breach, minimizing the impact.
Conclusion
The widespread breaches of executive Office 365 accounts underscore the critical need for enhanced cybersecurity measures within organizations. The financial and reputational consequences of such attacks are devastating, making proactive security a top priority. By implementing strong security practices, including robust multi-factor authentication, comprehensive employee training, and regular security assessments, companies can significantly reduce their risk of falling victim to these sophisticated attacks. Don't wait for an Office 365 breach to impact your business. Take immediate action to strengthen your cybersecurity defenses and protect your valuable data and executive accounts. Investing in robust Office 365 security is not an expense; it's an investment in the future of your organization.

Featured Posts
-
 Is A Transfer Away Best For Alejandro Garnachos Career
May 28, 2025
Is A Transfer Away Best For Alejandro Garnachos Career
May 28, 2025 -
 Pembangunan Taman Kota Di Balikpapan Wawali Susetyo Realisasikan 1 Hektare Per Kecamatan
May 28, 2025
Pembangunan Taman Kota Di Balikpapan Wawali Susetyo Realisasikan 1 Hektare Per Kecamatan
May 28, 2025 -
 Surya Paloh Ungkap Krisis Infrastruktur Jalan Raya Di Bali
May 28, 2025
Surya Paloh Ungkap Krisis Infrastruktur Jalan Raya Di Bali
May 28, 2025 -
 Dodgers Vs Diamondbacks Underdog Diamondbacks Chances For Victory
May 28, 2025
Dodgers Vs Diamondbacks Underdog Diamondbacks Chances For Victory
May 28, 2025 -
 Psv Amankan Gelar Liga Belanda Dengan Kemenangan 3 1 Atas Sparta Rotterdam
May 28, 2025
Psv Amankan Gelar Liga Belanda Dengan Kemenangan 3 1 Atas Sparta Rotterdam
May 28, 2025
