Executive Inbox Hacking: Millions In Losses, FBI Investigation Underway
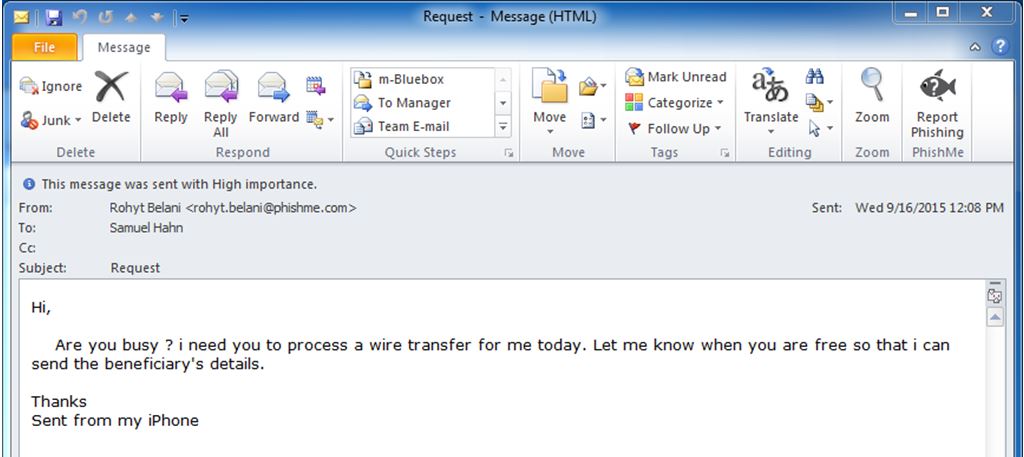
Table of Contents
Understanding the Mechanics of Executive Inbox Hacking
Executive inbox hacking, also known as Business Email Compromise (BEC), targets high-level executives to illicitly transfer funds or gain sensitive information. These attacks leverage various techniques, often relying on a combination of social engineering and technical exploits.
- Phishing and Spear Phishing: Attackers send deceptive emails that appear to be from legitimate sources, such as trusted colleagues, vendors, or even the CEO. Spear phishing campaigns are highly targeted, using information gleaned from social media or other sources to personalize the attack and increase its effectiveness.
- Common Attack Vectors:
- Spoofed emails meticulously mimic trusted sources, often using forged email addresses and logos.
- Compromised accounts are often accessed via credential stuffing (using stolen credentials from data breaches) or malware that secretly captures login details.
- Vulnerabilities in email systems, such as outdated software or weak security configurations, are exploited to gain unauthorized access.
- Sophisticated social engineering tactics, such as creating a sense of urgency or leveraging a known business relationship, manipulate victims into taking action.
- Malware and Ransomware: In some cases, attackers use malware to gain persistent access to the victim's system, allowing them to monitor email activity and intercept sensitive information. Ransomware may also be deployed to encrypt data and demand a ransom for its release.
The Financial Ramifications of Executive Email Compromise
The financial consequences of successful executive email compromise attacks are devastating. Victims often experience substantial losses, far beyond the immediate financial impact.
- Direct Financial Losses: Wire transfer fraud is a common tactic, with attackers instructing victims to send large sums of money to fraudulent accounts. Invoice manipulation, where attackers alter payment details on legitimate invoices, is another prevalent method. Data breaches can lead to significant costs associated with recovery, notification, and potential legal liabilities.
- Real-World Examples: Numerous cases have been reported where companies have lost millions of dollars due to BEC attacks. One prominent example involved a large manufacturing company losing over $5 million in a single fraudulent wire transfer.
- Indirect Costs: Beyond direct financial losses, businesses face indirect costs such as reputational damage, loss of investor confidence, decreased market value, legal fees, and the cost of restoring damaged systems and data.
- Illustrative Financial Impact:
- Loss of funds through fraudulent wire transfers, often in large sums.
- Substantial costs associated with data recovery, breach notification, and credit monitoring for affected individuals.
- Decreased investor confidence and a negative impact on the company's stock price.
- Potential legal penalties and fines for non-compliance with data protection regulations.
The FBI Investigation: Current Status and Implications
The FBI's Internet Crime Complaint Center (IC3) is actively investigating numerous cases of executive inbox hacking, highlighting the agency's commitment to combating this growing cybercrime threat. The investigations often involve collaboration with international law enforcement agencies to track down perpetrators and recover stolen funds.
- FBI Actions:
- Ongoing investigations into multiple incidents across various industries and countries.
- Collaboration with international law enforcement agencies to coordinate investigations and share intelligence.
- Focus on identifying and prosecuting perpetrators, often leading to significant prison sentences and financial penalties.
- Public awareness campaigns to educate businesses about the risks of BEC and best practices for prevention.
- Legal Consequences: Perpetrators of executive inbox hacking face severe penalties, including lengthy prison sentences, significant fines, and asset forfeiture.
Protecting Your Business from Executive Inbox Hacking
Protecting your business from executive inbox hacking requires a multi-layered approach that combines proactive security measures with comprehensive employee training.
- Preventative Measures:
- Implement Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring more than just a password to access accounts.
- Regular Security Awareness Training: Educate employees about phishing techniques, social engineering tactics, and best practices for identifying suspicious emails.
- Strong Password Policies: Enforce strong password policies and encourage the use of password management tools.
- Utilize Email Security Solutions: Implement robust email security solutions, including spam filters, anti-phishing software, and email authentication protocols like SPF, DKIM, and DMARC.
- Regular Security Audits and Penetration Testing: Conduct regular security audits and penetration testing to identify vulnerabilities in your systems and address them promptly.
- Develop Incident Response Plans: Create a detailed incident response plan outlining the steps to take in the event of a security breach.
Strengthening Your Defenses Against Executive Inbox Hacking
Executive inbox hacking poses a significant threat to businesses of all sizes, resulting in substantial financial losses and reputational damage. The FBI's ongoing investigations underscore the critical need for robust cybersecurity measures. The key takeaways from this article highlight the importance of proactive security measures, employee training, and the implementation of strong security protocols. Don't become a statistic. Take action now to protect your business from executive inbox hacking and its devastating consequences. Explore resources from the FBI's IC3 and other cybersecurity organizations to learn more about implementing best practices and staying ahead of evolving threats. Protecting your organization from this sophisticated form of cybercrime is crucial for long-term success and stability.

Featured Posts
-
 Gncc Mx Sx Flat Track And Enduro Your Source For Moto News
May 17, 2025
Gncc Mx Sx Flat Track And Enduro Your Source For Moto News
May 17, 2025 -
 Did Donald And Melania Trump Divorce A Look At Their Marriage
May 17, 2025
Did Donald And Melania Trump Divorce A Look At Their Marriage
May 17, 2025 -
 Motocross Enduro And More The Latest Moto News From Gncc Mx Sx And Flat Track
May 17, 2025
Motocross Enduro And More The Latest Moto News From Gncc Mx Sx And Flat Track
May 17, 2025 -
 Kak Vybrat Industrialniy Park Sovety Po Otsenke Konkurentsii
May 17, 2025
Kak Vybrat Industrialniy Park Sovety Po Otsenke Konkurentsii
May 17, 2025 -
 Ftcs Appeal Will The Microsoft Activision Merger Be Blocked
May 17, 2025
Ftcs Appeal Will The Microsoft Activision Merger Be Blocked
May 17, 2025
