Crook's Office365 Hacking Spree Nets Millions: Federal Authorities Investigate

Table of Contents
The Scale of the Office365 Hacking Operation
The financial losses resulting from this widespread Office365 hacking incident are staggering. While precise figures are still emerging as the investigation unfolds, early estimates suggest losses exceeding tens of millions of dollars. This represents a significant blow to numerous businesses, impacting their operations, reputation, and financial stability.
Financial Losses
- Total estimated losses: While the exact figure remains undisclosed pending the completion of the federal investigation, estimates from affected businesses suggest a minimum of $30 million in collective losses.
- Number of businesses affected: Initial reports indicate hundreds of businesses of varying sizes have been targeted across the United States. The true number is likely higher, with many smaller businesses yet to report incidents.
- Types of businesses targeted: The hackers appear to have targeted a diverse range of businesses, from small and medium-sized enterprises (SMEs) to larger corporations, demonstrating a lack of discrimination in their attack strategy. Industries affected include healthcare, finance, and retail.
- Geographic areas most impacted: While the investigation is ongoing, reports suggest a concentration of affected businesses in major metropolitan areas across the East Coast and Midwest.
Methods Used in the Office365 Hack
The hackers responsible for this devastating Office365 security breach employed a combination of sophisticated phishing techniques and exploitation of known vulnerabilities within the Microsoft 365 platform.
Phishing and Social Engineering
The primary method of gaining access appears to be through highly targeted phishing emails designed to trick employees into revealing their credentials.
- Detailed explanation of phishing techniques: Hackers used convincing email spoofing, creating emails that mimicked legitimate communications from known contacts or services. These emails often contained malicious links or attachments.
- Description of social engineering tactics: Beyond simple phishing, the attackers appear to have utilized social engineering tactics, such as creating a sense of urgency or exploiting human error to increase the chances of success.
- Examples of malicious links or attachments: Malware-laden attachments and links leading to credential-harvesting websites were frequently employed, bypassing many standard email security filters.
Exploiting Vulnerabilities
While details about specific vulnerabilities are still under investigation, it is highly likely the hackers exploited known security flaws in Microsoft 365 or third-party applications integrated with it. The failure to implement security patches and updates likely played a significant role.
- Specific vulnerabilities potentially exploited: The investigation is focusing on vulnerabilities related to authentication mechanisms and data access controls. It is likely outdated versions of software were exploited.
- Importance of regular software updates and patching: Maintaining up-to-date software is critical in mitigating risks associated with known vulnerabilities.
- Discussion of multi-factor authentication's role in preventing such attacks: Implementing multi-factor authentication (MFA) is crucial to prevent unauthorized access even if credentials are compromised.
The Federal Investigation
Multiple federal agencies are actively investigating this widespread Office365 hacking incident.
Agencies Involved
The Federal Bureau of Investigation (FBI) is leading the investigation, collaborating with other relevant agencies, including the Cybersecurity and Infrastructure Security Agency (CISA).
- Statement from the investigating agency: While a formal public statement is yet to be released, sources suggest the FBI is treating this as a high-priority case due to the scale and sophistication of the operation.
- Timeline of the investigation: The investigation is still in its early stages, with the timeline expected to extend for several months.
- Potential charges against the perpetrators: Depending on the evidence gathered, perpetrators face potential charges including wire fraud, identity theft, and computer hacking, which could lead to lengthy prison sentences and substantial fines.
Potential Outcomes
The outcome of this investigation will have significant implications for both businesses and cybersecurity practices.
- Potential sentences for those responsible: Severe penalties are expected, serving as a strong deterrent to future cybercriminals.
- Increased security awareness and legislation: This incident is likely to increase public and political awareness around the importance of robust cybersecurity measures, potentially leading to new legislation and regulations.
- Changes expected within Microsoft 365 security protocols: Microsoft is expected to review and enhance its security protocols in response to the vulnerabilities exploited in this attack.
Protecting Your Business from Office365 Hacks
Businesses must take proactive steps to mitigate the risk of similar attacks.
Best Practices
- Implementing strong password policies: Enforce strong, unique passwords and encourage regular password changes.
- Utilizing multi-factor authentication (MFA): MFA adds an extra layer of security, making it much harder for hackers to gain unauthorized access.
- Regularly updating software and security patches: Stay current with software updates and security patches to address known vulnerabilities.
- Conducting regular security awareness training for employees: Educate employees on phishing techniques and social engineering tactics to reduce the risk of human error.
- Investing in robust cybersecurity solutions: Consider investing in advanced security solutions such as endpoint detection and response (EDR) and security information and event management (SIEM) systems.
Conclusion
This large-scale Office365 hacking spree demonstrates the critical need for heightened cybersecurity awareness and proactive measures to protect businesses from cyber threats. The significant financial losses and ongoing federal investigation underscore the severity of the situation. Don't become the next victim of an Office365 hacking spree. Invest in robust cybersecurity measures and employee training today. Secure your Microsoft 365 environment and protect your valuable data. Implement multi-factor authentication, regularly update your software, and educate your employees about phishing techniques. Proactive security is your best defense against the ever-evolving landscape of cybercrime.

Featured Posts
-
 Shohei Ohtani Rises To The Challenge A 2 Run Home Run In Japan
May 18, 2025
Shohei Ohtani Rises To The Challenge A 2 Run Home Run In Japan
May 18, 2025 -
 City Pickles Brooklyn Pickleball Complex A 60 000 Sq Ft Game Changer
May 18, 2025
City Pickles Brooklyn Pickleball Complex A 60 000 Sq Ft Game Changer
May 18, 2025 -
 Kanye West Taylor Swift And The Super Bowl Controversy
May 18, 2025
Kanye West Taylor Swift And The Super Bowl Controversy
May 18, 2025 -
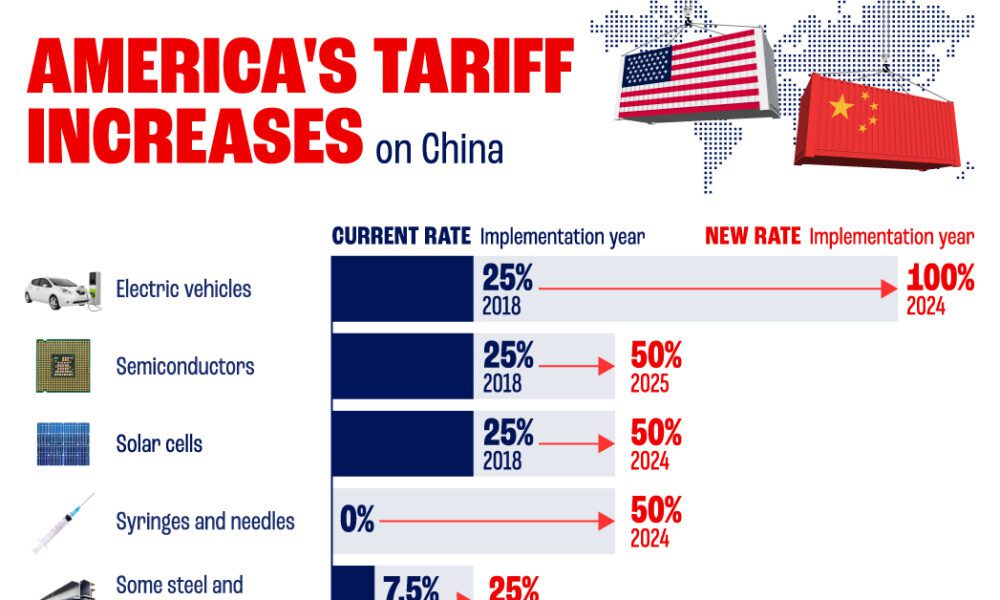 30 Tariffs On Chinese Goods The Trump Legacy Until 2025
May 18, 2025
30 Tariffs On Chinese Goods The Trump Legacy Until 2025
May 18, 2025 -
 Armstrongs Double Blast Leads Cubs To Series Win Against Dodgers
May 18, 2025
Armstrongs Double Blast Leads Cubs To Series Win Against Dodgers
May 18, 2025
