Hacker's Multi-Million Dollar Office365 Scam Exposed
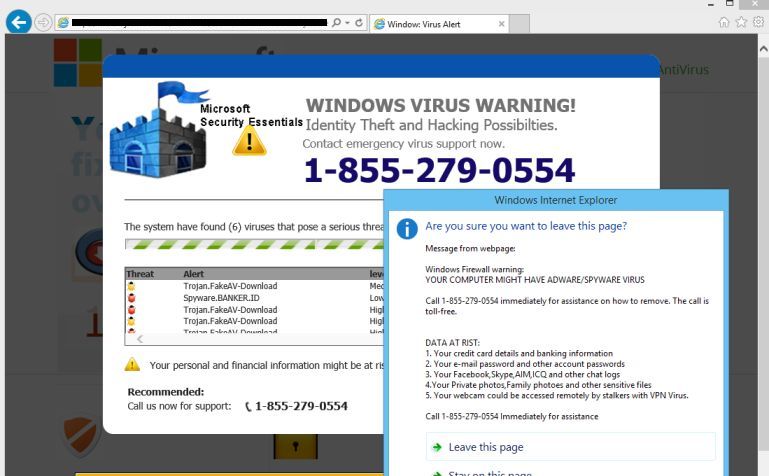
Table of Contents
The Mechanics of the Office365 Scam
This intricate Office365 scam leverages a combination of sophisticated techniques to gain unauthorized access and exfiltrate sensitive data.
Phishing and Social Engineering
The initial breach often begins with phishing and social engineering attacks. Hackers employ deceptive tactics to trick unsuspecting users into revealing their credentials or clicking malicious links.
- Types of phishing emails: These scams often mimic legitimate invoices, password reset requests, or urgent notifications from seemingly trusted sources. A common tactic is to create a sense of urgency to pressure the recipient into immediate action without careful consideration.
- Successful social engineering techniques: Hackers may impersonate IT staff, executives, or even clients to manipulate users into providing sensitive information or granting access to systems. They might exploit human psychology by preying on trust, fear, or curiosity. This involves carefully crafting emails and messages that appear legitimate and urgent. Keyword integration: Office365 phishing, social engineering attacks, email compromise.
Exploiting Vulnerabilities
Beyond social engineering, the Office365 scam often exploits known vulnerabilities in the platform or weaknesses in user security practices.
- Specific software vulnerabilities: Out-of-date software versions and unpatched security flaws within Office365 applications can provide entry points for hackers. Regular updates are crucial to mitigate these risks.
- Weak passwords and lack of multi-factor authentication: Using simple, easily guessable passwords or failing to enable multi-factor authentication (MFA) significantly increases vulnerability. MFA adds an extra layer of security, requiring multiple forms of verification before granting access.
- Keyword integration: Office365 vulnerabilities, security flaws, password security.
Data Exfiltration Techniques
Once access is gained, hackers employ various methods to exfiltrate valuable data.
- Methods used to steal data: This can involve the use of malware to steal credentials or sensitive information, exploiting compromised accounts, or directly accessing data through vulnerabilities.
- Types of data stolen: The stolen data often includes financial records, customer information, intellectual property, and confidential business communications. This data can be used for identity theft, financial fraud, corporate espionage, or blackmail.
- Keyword integration: data exfiltration, data breach, cybersecurity.
The Financial Impact of the Office365 Scam
The financial consequences of falling victim to this Office365 scam can be catastrophic.
Monetary Losses
The monetary losses incurred by victims can range from thousands to millions of dollars.
- Total financial losses: The aggregate cost of these scams across numerous victims amounts to millions of dollars annually.
- Average loss per victim: While the average loss per victim can vary depending on the scale of the breach, the costs include direct financial theft, legal fees, remediation costs (restoring data and systems), and the cost of dealing with the reputational damage.
- Keyword integration: financial losses, Office365 data breach costs, cybercrime costs.
Reputational Damage
Beyond direct financial losses, the reputational damage suffered by victims can be equally devastating.
- Loss of customer trust: A data breach can severely damage a company's reputation, leading to a loss of customer trust and potential business.
- Negative publicity: News of a data breach can attract negative media attention, further harming the company's reputation and potentially driving away customers.
- Impact on business operations: The disruption caused by a data breach can significantly impact business operations, leading to lost productivity and revenue.
- Keyword integration: reputational damage, brand damage, cybersecurity reputation.
Protecting Yourself from Office365 Scams
Proactive measures are crucial to mitigate the risk of falling victim to Office365 scams.
Best Practices for Office365 Security
Implementing robust security measures is paramount.
- Enable multi-factor authentication: This is crucial to prevent unauthorized access even if passwords are compromised.
- Use strong, unique passwords: Utilize complex passwords that are difficult to guess, and use a different password for every account.
- Regularly update software: Ensure all software, including Office365 applications and operating systems, is up-to-date with the latest security patches.
- Implement security awareness training for employees: Educate employees about phishing scams, social engineering tactics, and safe internet practices.
- Use reputable security software: Invest in robust antivirus and anti-malware software to protect your systems from threats.
- Keyword integration: Office365 security best practices, cybersecurity tips, preventing Office365 breaches.
Responding to a Suspected Breach
If a breach is suspected, immediate action is vital.
- Immediately change passwords: Change all passwords associated with affected accounts as quickly as possible.
- Contact your IT department: Report the suspected breach to your IT department for immediate investigation and remediation.
- Report the incident to authorities: Contact law enforcement and relevant regulatory bodies to report the incident.
- Investigate the extent of the damage: Conduct a thorough investigation to determine the scope of the breach and the type of data compromised.
- Keyword integration: Office365 breach response, incident response plan, data breach recovery.
Conclusion
The multi-million dollar Office365 scam underscores the critical need for robust cybersecurity measures. The devastating financial and reputational consequences highlight the importance of proactive security practices. Don't become the next victim of an Office365 scam. Implement robust security measures today to safeguard your valuable data and protect your business from devastating financial and reputational losses. For further information on Office365 security and best practices, consult reputable cybersecurity resources and your IT department.

Featured Posts
-
 Todays Stock Market Key Developments Trumps Tariffs And Uk Trade Deal
May 11, 2025
Todays Stock Market Key Developments Trumps Tariffs And Uk Trade Deal
May 11, 2025 -
 Halls Crossroads Baseball Tournament Honors Chris Newsom
May 11, 2025
Halls Crossroads Baseball Tournament Honors Chris Newsom
May 11, 2025 -
 Aaron Judge Ties Babe Ruths Yankees Record A Historic Feat
May 11, 2025
Aaron Judge Ties Babe Ruths Yankees Record A Historic Feat
May 11, 2025 -
 Controversia En La Formula 1 Las Polemicas Palabras De Un Piloto Argentino Sobre Uruguay
May 11, 2025
Controversia En La Formula 1 Las Polemicas Palabras De Un Piloto Argentino Sobre Uruguay
May 11, 2025 -
 Did Benny Blanco Cheat Selena Gomez Theresa Marie And The Online Speculation
May 11, 2025
Did Benny Blanco Cheat Selena Gomez Theresa Marie And The Online Speculation
May 11, 2025
