Significant Office365 Data Breach Results In Millions Of Dollars In Losses
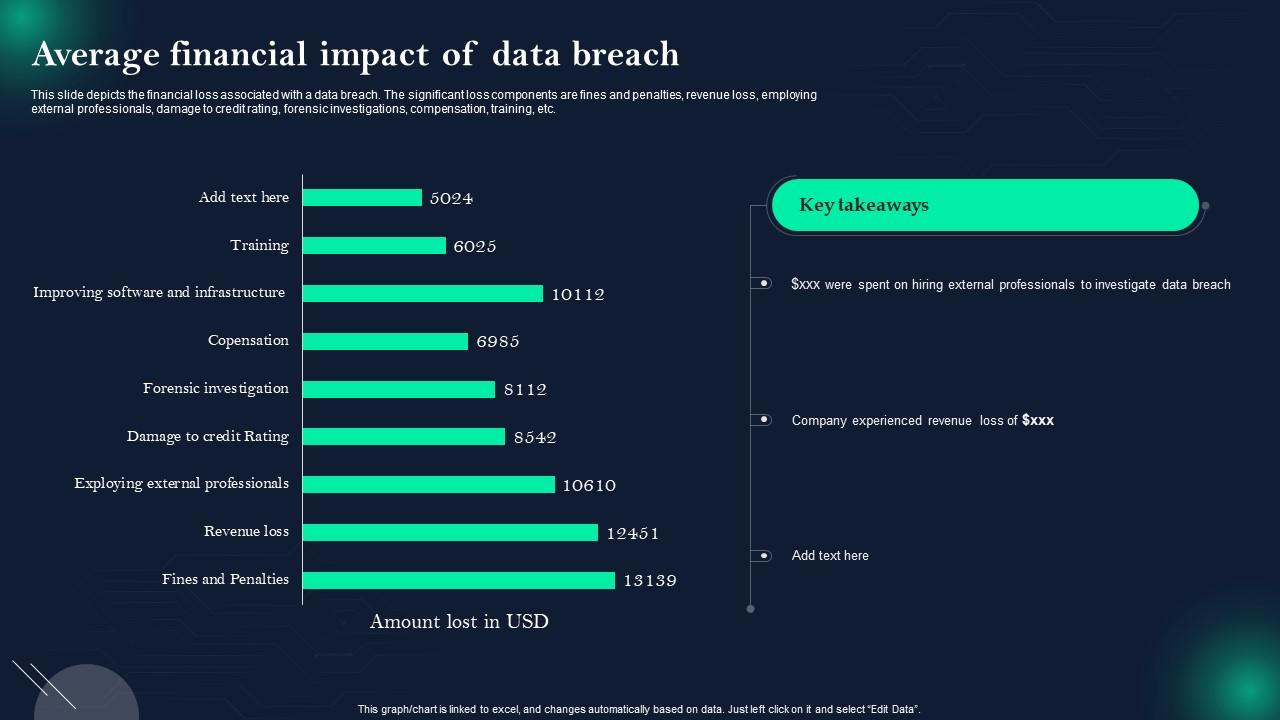
Table of Contents
H2: The Rising Threat of Office365 Data Breaches
H3: Vulnerabilities Exploited by Cybercriminals
Cybercriminals exploit various vulnerabilities in Office365 to gain unauthorized access to sensitive data. Common attack vectors include:
- Phishing Emails: Deceptive emails designed to trick users into revealing their credentials or downloading malware. These often mimic legitimate communications from trusted sources.
- Compromised Credentials: Stolen or weak passwords, often obtained through phishing or brute-force attacks, provide direct access to Office365 accounts. Reusing passwords across multiple platforms significantly increases this vulnerability.
- Malicious Apps: Unauthorized apps installed within Office365 can steal data or provide backdoor access to an organization's network. Lack of proper app vetting and permissions management contributes to this risk.
Recent high-profile Office365 breaches highlight the severity of the problem. For example, [Insert example of a recent breach, citing source]. These breaches often result in the theft of:
- Customer data (names, addresses, contact information, payment details)
- Financial records (bank account numbers, transaction history)
- Intellectual property (designs, patents, confidential business information)
H3: The Cost of an Office365 Data Breach
The financial impact of an Office365 data breach extends far beyond the immediate costs. Direct losses include:
- Legal fees: Responding to lawsuits and regulatory investigations.
- Regulatory fines: Penalties imposed by authorities for non-compliance with data protection regulations (e.g., GDPR, CCPA).
- Recovery costs: Restoring data, improving security infrastructure, and notifying affected individuals.
Indirect costs are equally significant and often harder to quantify:
- Loss of reputation: Damage to brand image and customer trust.
- Customer churn: Loss of existing customers due to the breach.
- Decreased productivity: Time spent investigating the breach and implementing remediation measures.
Consider the case of [Insert example of a company that suffered significant losses, quantifying the damage if possible, and citing the source]. Their Office365 data breach resulted in [quantifiable loss, e.g., "$X million in direct costs and a Y% drop in stock price"]. Beyond direct financial losses, the cost of cybersecurity insurance and professional remediation services can also be substantial.
H2: Understanding the Impact of a Major Office365 Data Breach
H3: Reputational Damage and Loss of Customer Trust
A data breach can inflict severe reputational harm, eroding customer trust and leading to long-term consequences:
- Loss of market share: Competitors may gain advantage.
- Negative media coverage: Publicity can damage the brand's image.
- Difficulty attracting new clients: Potential customers may be hesitant to work with a compromised organization.
H3: Legal and Regulatory Compliance Penalties
Organizations failing to adequately protect sensitive data face severe legal and regulatory consequences. Non-compliance with regulations such as:
- GDPR (General Data Protection Regulation)
- CCPA (California Consumer Privacy Act)
- HIPAA (Health Insurance Portability and Accountability Act)
can result in hefty fines and penalties:
- Significant financial penalties
- Legal action from affected individuals
- Reputational damage
H2: Protecting Your Organization from Office365 Data Breaches
H3: Implementing Robust Security Measures
Proactive security measures are crucial for preventing Office365 data breaches. These include:
- Multi-factor authentication (MFA): Adds an extra layer of security, requiring multiple forms of authentication to access accounts.
- Strong password policies: Enforcing complex passwords and regular password changes.
- Regular security awareness training: Educating employees about phishing scams and other cybersecurity threats.
- Advanced threat protection tools: Detecting and preventing sophisticated cyberattacks.
- Data loss prevention (DLP) solutions: Preventing sensitive data from leaving the organization's control.
- Regular security audits and vulnerability assessments: Identifying and addressing security weaknesses.
H3: Developing an Incident Response Plan
A comprehensive incident response plan is essential for minimizing the damage caused by a data breach:
- Establish clear communication protocols
- Define roles and responsibilities
- Outline steps for data recovery and containment
- Include procedures for notifying affected individuals and regulatory bodies
- Coordinate with legal counsel and cybersecurity experts
3. Conclusion
Office365 data breaches pose a significant threat to organizations, resulting in substantial financial losses and irreparable reputational damage. The cost of an Office365 data breach encompasses direct expenses like legal fees and regulatory fines, as well as indirect costs such as reputational harm and loss of customer trust. Protecting your organization requires implementing robust security measures, including MFA, strong password policies, and regular security awareness training. A comprehensive incident response plan is equally crucial. Protect your business from the devastating impact of an Office365 data breach – implement strong security protocols today! Ignoring Office365 security is simply not an option in today's interconnected world.

Featured Posts
-
 The Countrys Top Business Locations A Data Driven Map
Apr 28, 2025
The Countrys Top Business Locations A Data Driven Map
Apr 28, 2025 -
 Aaron Judge Equals Babe Ruths Legendary Yankees Record
Apr 28, 2025
Aaron Judge Equals Babe Ruths Legendary Yankees Record
Apr 28, 2025 -
 T Mobile Data Breaches 16 Million Penalty Highlights Security Gaps
Apr 28, 2025
T Mobile Data Breaches 16 Million Penalty Highlights Security Gaps
Apr 28, 2025 -
 Us Citizen Age 2 Faces Deportation Federal Judge Sets Hearing
Apr 28, 2025
Us Citizen Age 2 Faces Deportation Federal Judge Sets Hearing
Apr 28, 2025 -
 Where To Invest Mapping The Countrys Top Business Hot Spots
Apr 28, 2025
Where To Invest Mapping The Countrys Top Business Hot Spots
Apr 28, 2025
Latest Posts
-
 Become Baba Yaga A John Wick Themed Las Vegas Experience
May 12, 2025
Become Baba Yaga A John Wick Themed Las Vegas Experience
May 12, 2025 -
 Ufc Flyweight Champion Shevchenko Ignores Fiorots Challenge
May 12, 2025
Ufc Flyweight Champion Shevchenko Ignores Fiorots Challenge
May 12, 2025 -
 John Wick And Baba Yaga Your Las Vegas Adventure Awaits
May 12, 2025
John Wick And Baba Yaga Your Las Vegas Adventure Awaits
May 12, 2025 -
 Shevchenko Vs Fiorot The Ufc Champs Blunt Rejection
May 12, 2025
Shevchenko Vs Fiorot The Ufc Champs Blunt Rejection
May 12, 2025 -
 Valentina Shevchenko Dismisses Manon Fiorots Callout
May 12, 2025
Valentina Shevchenko Dismisses Manon Fiorots Callout
May 12, 2025
